Scan Methods
Active Scan
Burp Bounty Pro gives you the ability to create your own vulnerability profiles to the active scanner.
The philosophy behind Burp Bounty’s active profiles is simple:
Profile payloads are inserted at the selected insertion points and the request is sent it to the server. Another option is use Raw request and sent it to the server.
In the HTTP response looks for a pattern (or patterns) with all the filtering options in the profiles.
Operation:
The request insertion points are extracted.
All active profiles are executed.
If there is a vulnerability, it’s reported.
If you scan one or multiple requests with the Active scan, you will launch against the request all the profiles that are active in the tab “Profiles-> Active Profiles”. If you scan a request, several request or one entire domain with “Active Scan->Some TAG”, the profiles that are tagged with “Some TAG” will be launched on that request/requests. For example, if you scan with Active Scan->XSS, the profiles tagged with the XSS tag will be launched on the request/requests.
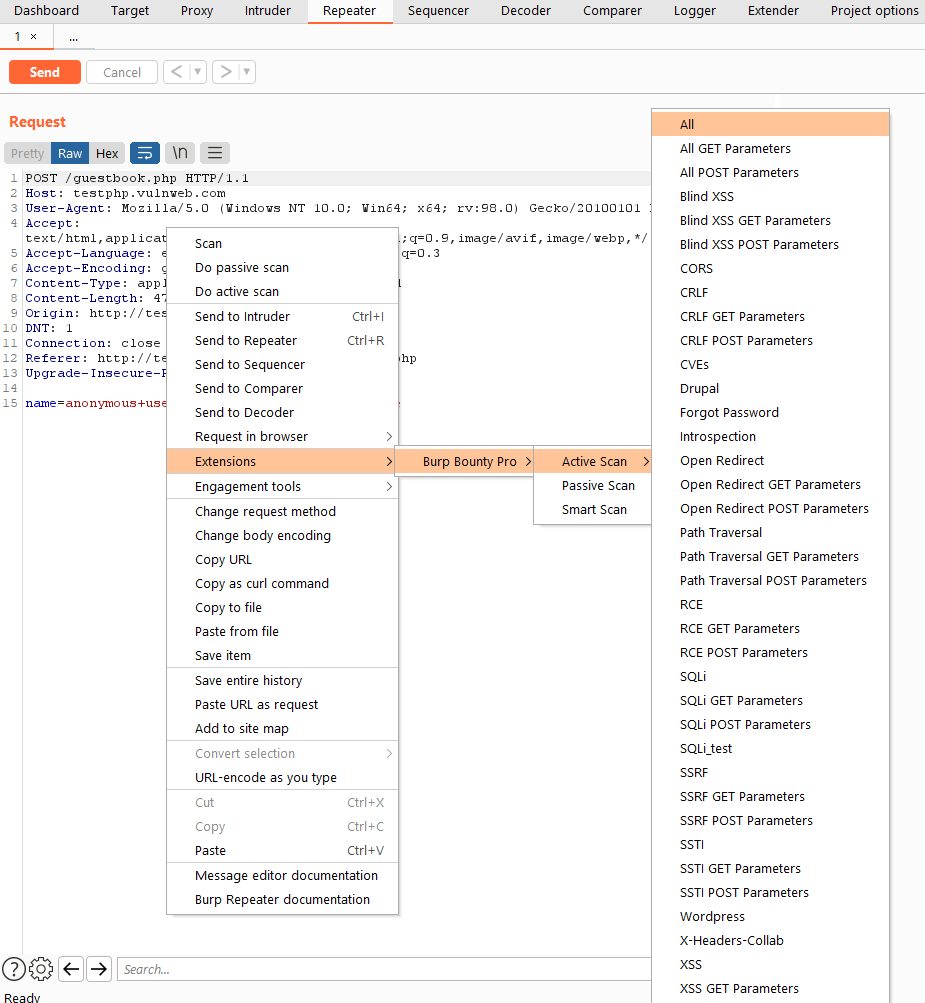

Right click and “Active Scan->XSS”
The profiles with the Tag “XSS” will be launched. For example, the “Test XSS append” and “XSS” profiles.
You can create new tags and create your own profiles groups for be launched to a target.
Passive Scan
The passive scanner doesn’t interact with HTTP traffic. Searches for patterns (or absence of them) in HTTP requests and responses.
A pattern is information detected through strings or a regular expression. If it detects a pattern, you get an alert.
If you scan one or multiple requests with the Passive scan, you will launch against the request/response the profiles that are active in the tab “Profiles-> Passive Request Profiles” and “Profiles-> Passive Response Profiles”. This scanner does not perform any request against the target, it only analyses the request/responses passively.
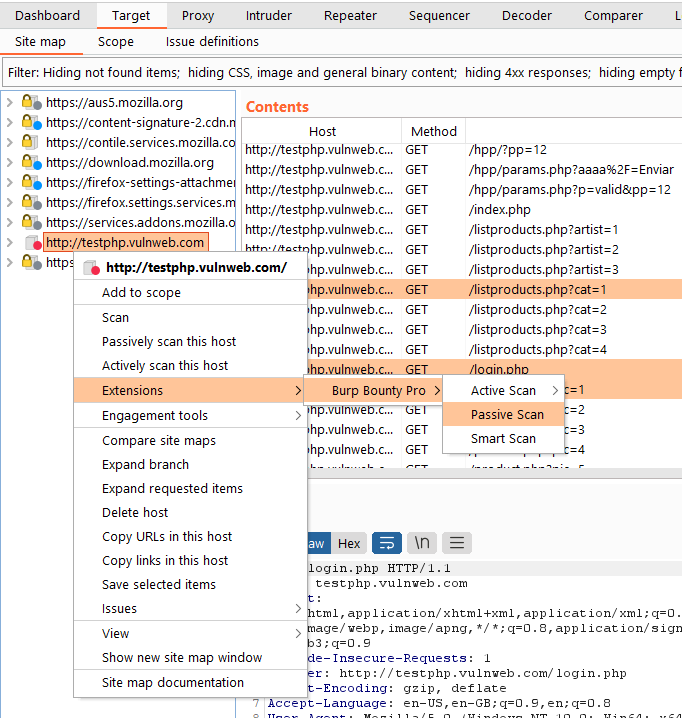
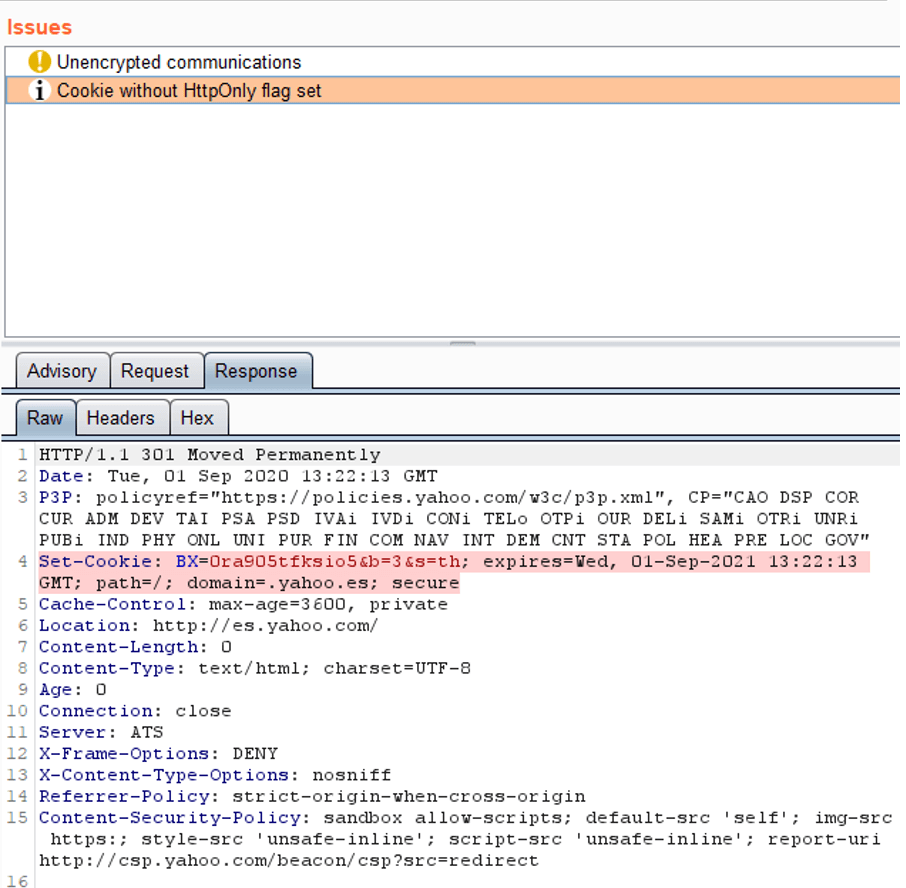
In this image you can see how an alert has been generated for the absence of a pattern. In this case, a Set cookie is detected, without HTTP only attribute set.
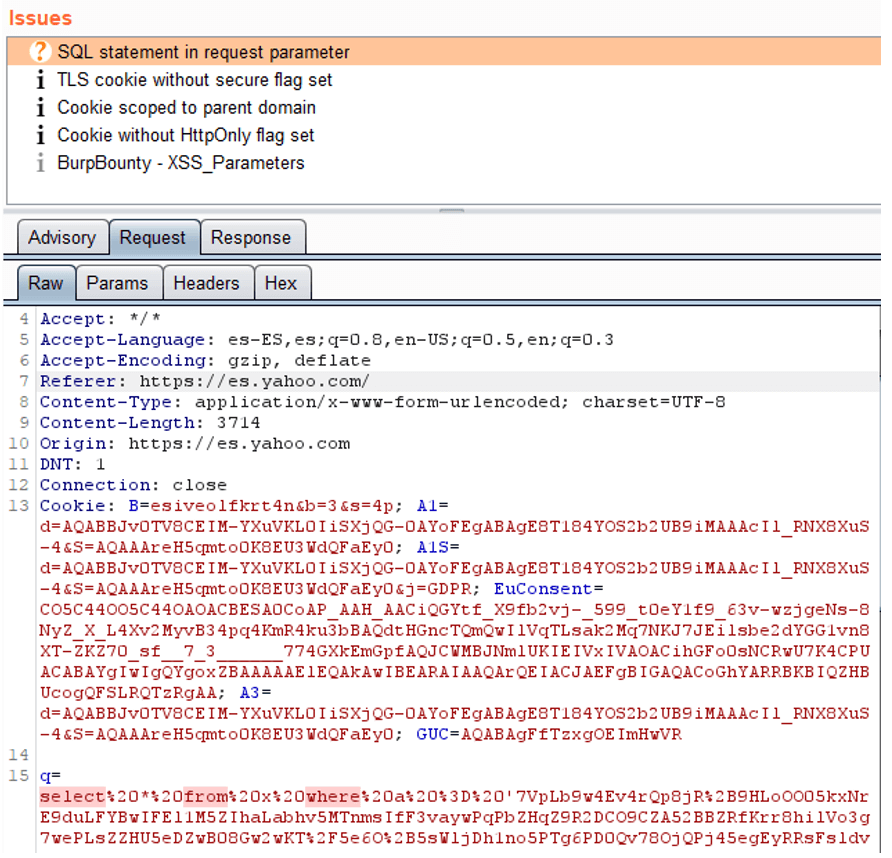
In next image, you can see how it detects an SQL statement in The HTTP Request. As you can see below, a “select” is detected followed by a “from” followed by “where”.
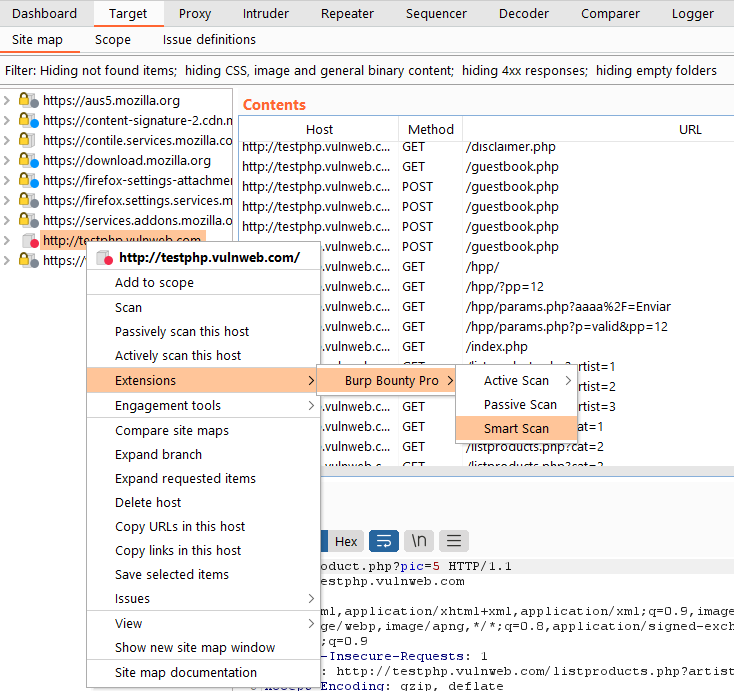
Smart Scan
If you scan a request or a domain with Smart Scan, attacks will be launched based on the enabled rules in the “Rules” section
The Smart Scan is a scanner that uses Burp Bounty Pro profiles to perform automatic attacks simulating the attacks that you would perform manually in a web application.
That is, if it detects an open redirect parameter, for example redirect_url, it will launch open redirect attacks only for that parameter.
You can create a rule to launch the automatic WordPress attacks, only when it has detected that the application you are analysing is a WordPress.
The logic is simple:
You create a passive profile or several
You create an active profile or several
You create a rule, where you specify:
If you detect that Passive Profiles have generated an alert
Launches Active Profiles against the host that generated the alerts
If successful, it will generate an automatic alert
Create a rule:
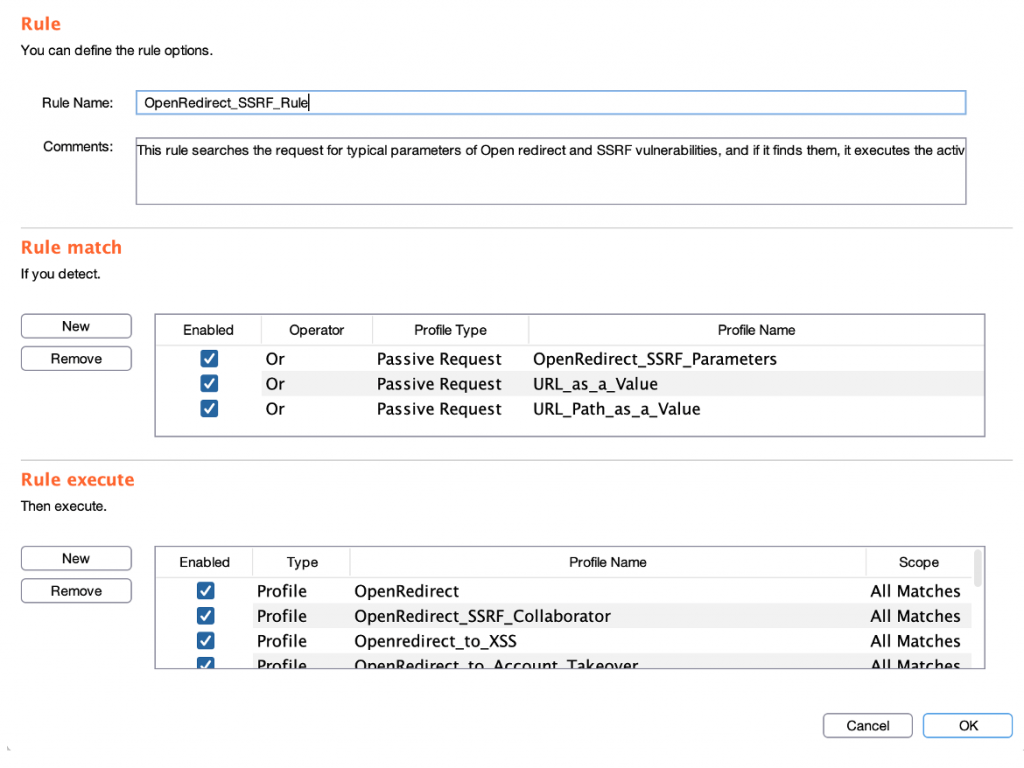
Rules section:

Live Passive Scan
If you want to activate the live passive scanner by default, you can do it through the “Options” tab with “Live Passive Scan” button.

Last updated