Passive Request Profiles
Burp Bounty Pro gives you the ability to create your own vulnerability profiles to the passive scanner.
Passive Request Scanner: Look for strings/regex (or the absence of them) in HTTP requests.
Next let’s see how passive request profiles are created to look for something (or the absence of it) in the HTTP request.
Step 1 (Required): The name and author of the profile are first set.
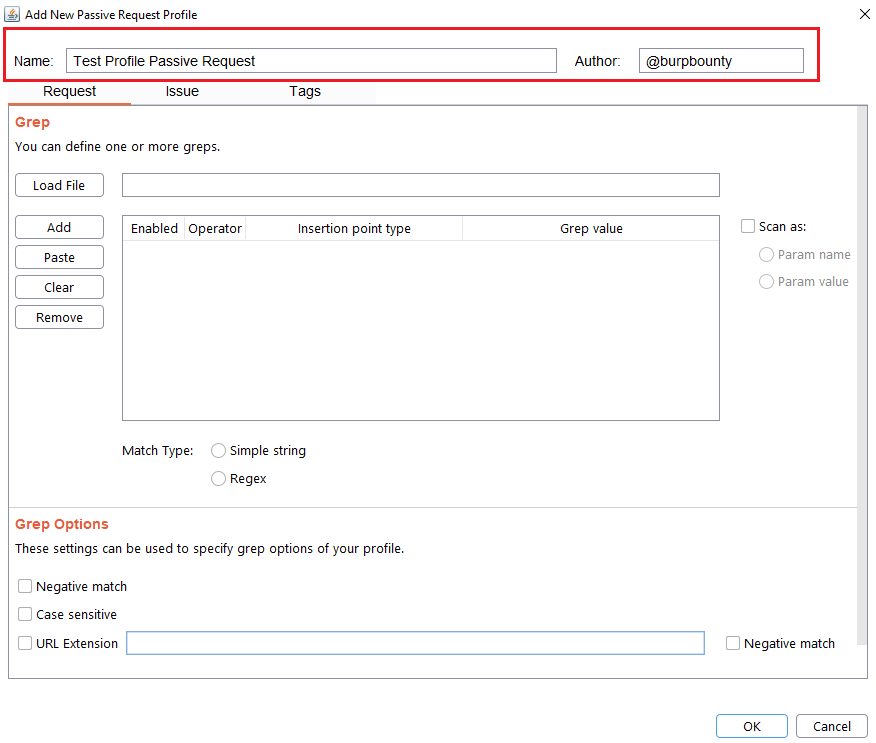
Step 2 (Required): Specifies the pattern or patterns to search in the request.
You can add the pattern by click on the “add” button and modifying the value, or by pasting it directly with the “Paste” button if you already have it in the clipboard.
You can also load a patterns file (one per line) with the “Load file” button.
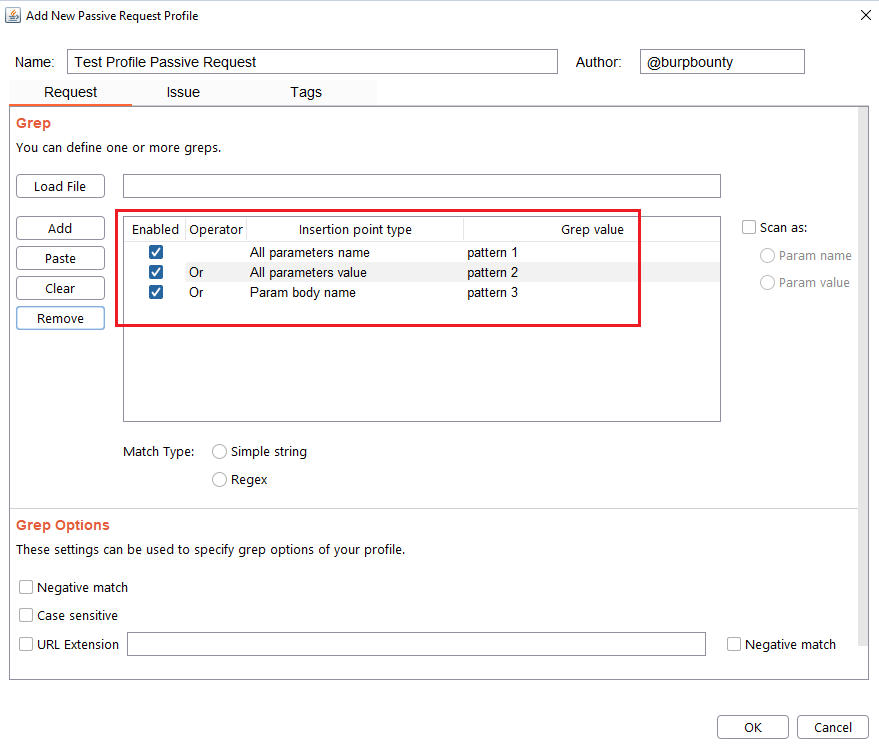
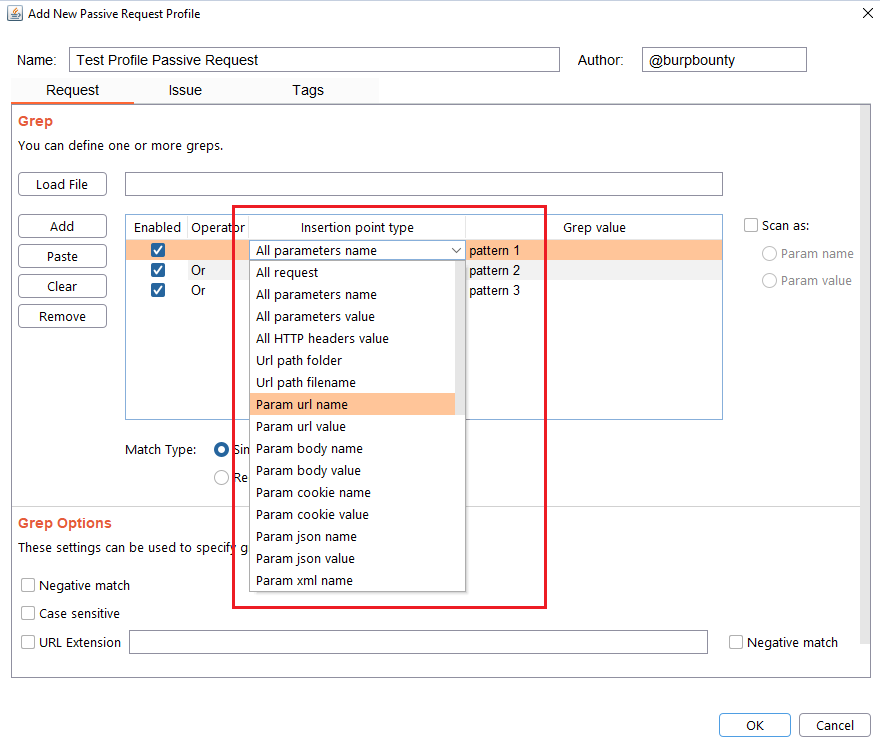
In this section you can choose in which insertion point you want to search for the pattern.
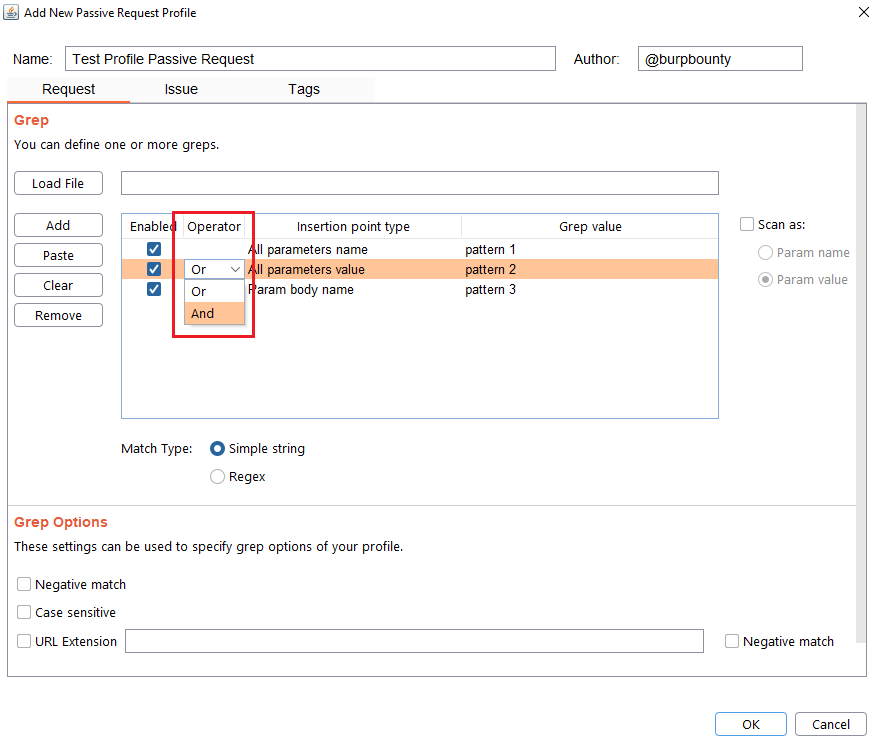
At the same time, the logical AND operator can be used when searching for a value. This allows us to further refine the profile and avoid false positives.
Step 3 (Optional): The passive request profile can be used for the Smart Scan. Two types of options:
Param name: the insertion point type name will be scanned with the active profiles selected in a rule.
Param value: the insertion point type value will be scanned with the active profiles selected in a rule.
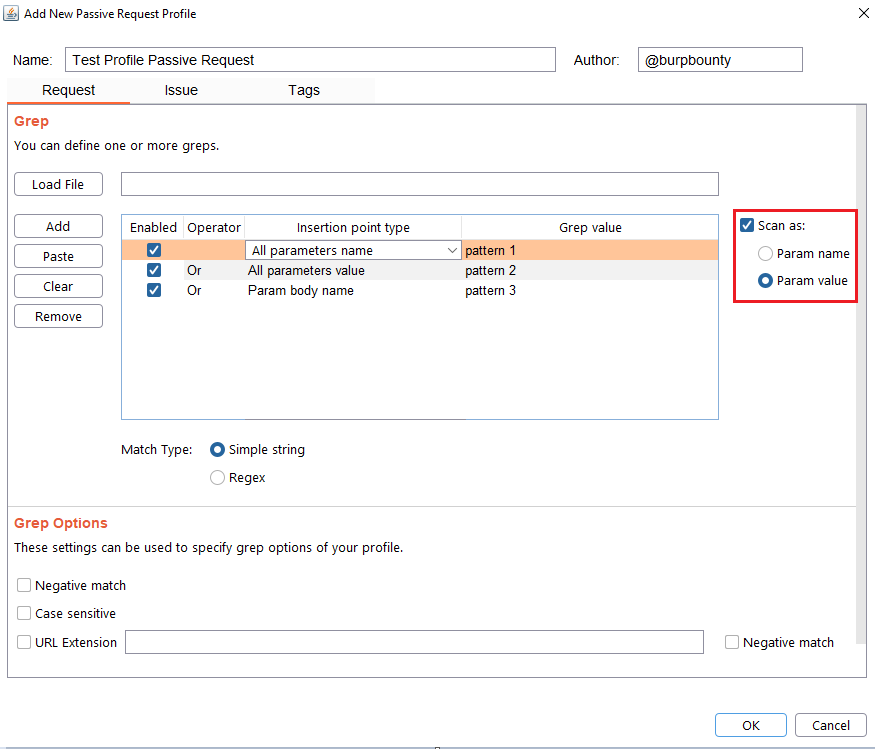
Note, that this step is not necessary if you only want to look for a pattern in the request and that it shows you an alert.
Step 4 (Required): Specifies which type of pattern to search in the insertion point.
Simple string
Regular expression
In this section you specify, if in the insertion point you want to search for a simple string or a regular expression.
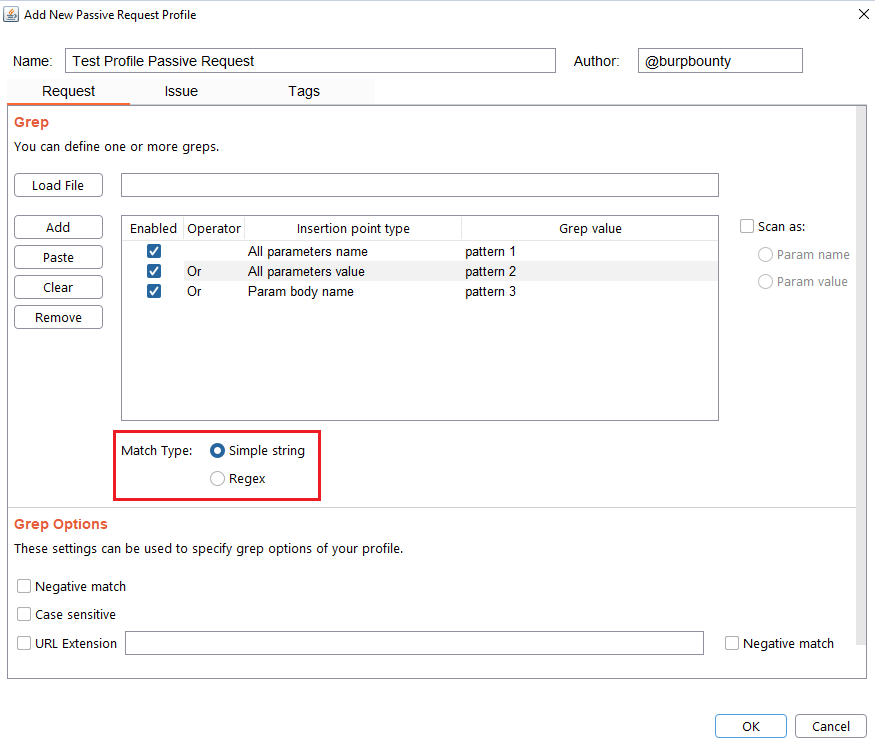
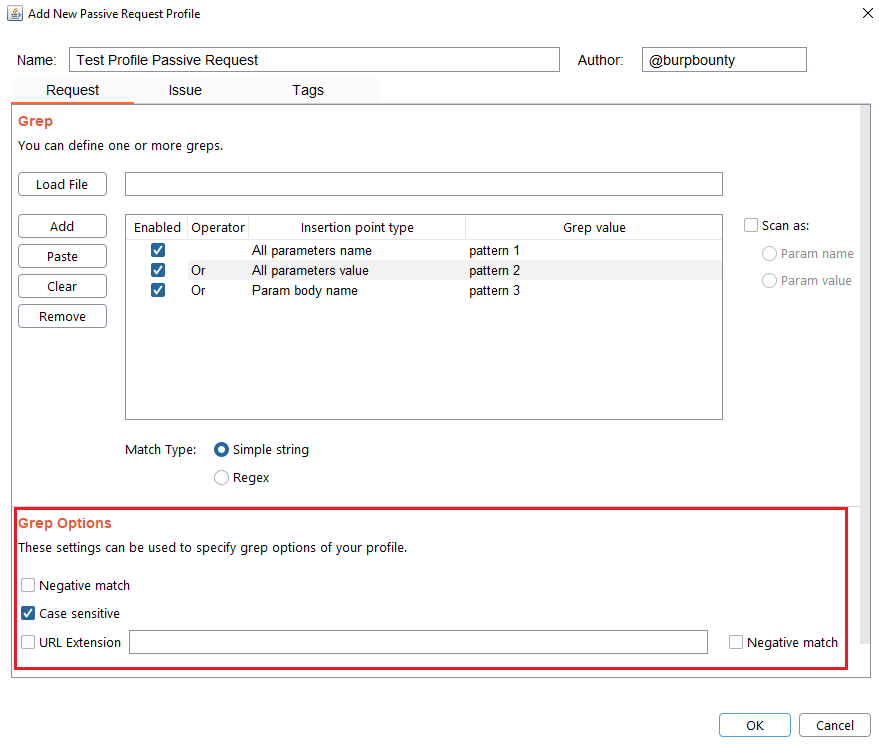
Step 5 (Optional): Grep options are specified.
Negative match: It will show you the alert, if the pattern you have set is not present in the insertion point that you have chosen.
Case sensitive: The pattern will be searched in the insertion point considering that it’s case sensitive.
URL Extension: It will only search for patterns if the extension of the URL to which the request is made, matches the extension or extensions specified in this field (for example, php or jsp, etc) or if it doesn’t match (negative match checkbox)
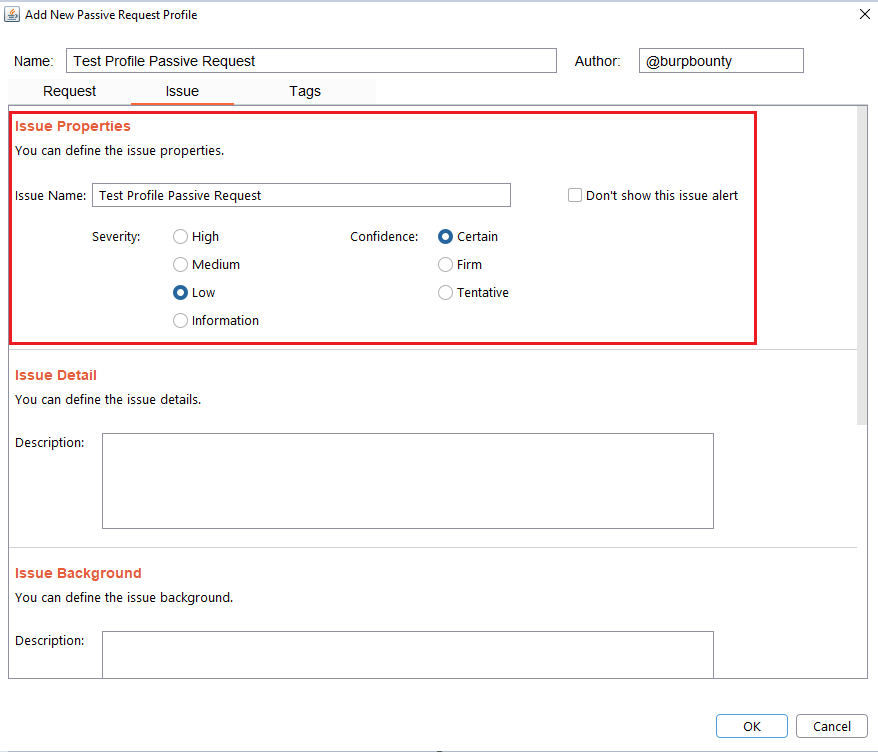
Step 6 (Required): It specifies the name that will appear in the alert and the criticality of that alert.
It’s necessary for the issue to appear, give it a “Issue Name” and complete the two fields, both the “severity” and the “confidence”. The issue descriptions are optional.
Step 7 (Optional): A tag is created and assigned to the profile. This is useful for better organization of profiles.
Last updated